KARAN PUNIANI, Staff Test Engineer at Micron Technology
The semiconductor industry is the backbone of modern technology, driving everything from smartphones to essential infrastructure systems. As these devices become more complex, the need to keep them secure is more critical than ever. One of the ways this is done is through adherence to security standards like FIPS (Federal Information Processing Standards) and ISO 27001, which have become key players in how firmware validation is done for semiconductor devices. These standards set up frameworks to ensure that the security protocols embedded in firmware are tested and confirmed to withstand the
ever-changing cyber threats. This article takes a look at how these security standards impact firmware validation, the benefits they bring, the challenges manufacturers face, and what the future holds in securing semiconductor devices.
Understanding key security standards
FIPS, especially FIPS 140-2/3, is one of the cornerstones for ensuring the security of semiconductor devices (FIGURE 1). It sets cryptographic requirements that must be met for devices handling sensitive data, making sure that devices used in high-security environments follow strict rules for encryption, key management, and secure data storage. This is a big deal for industries like defense, healthcare, and finance, where security is non-negotiable. On the flip side, ISO 27001 provides a broader perspective, focusing on how an organization manages and protects data throughout its lifecycle. It plays a significant role in how semiconductor manufacturers approach firmware validation by pushing them to implement solid risk assessments, vulnerability checks, and ongoing improvements to maintain high levels of security
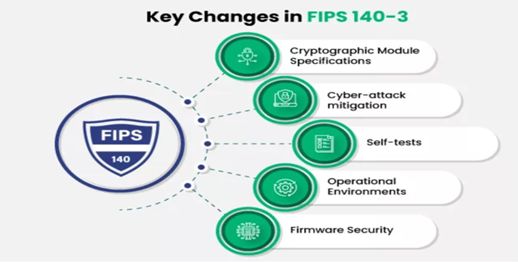
Influence on firmware development and testing
FIPS and ISO 27001 influence every stage of the firmware development process, from design to testing. During development, these standards require secure coding practices, strong encryption algorithms, and methods to prevent unauthorized access to firmware. For instance, FIPS 140-2/3 demands the use of certified cryptographic modules, which directly affects the selection of hardware and software components in semiconductor devices. ISO 27001 also pushes manufacturers to create secure development environments and conduct regular risk assessments to spot vulnerabilities early in the design phase.
Once the firmware is developed, it’s time to validate it. Both FIPS and ISO 27001 lay out the groundwork for rigorous testing, including penetration testing, vulnerability scanning, and audits, to confirm that the firmware is following the required security protocols. Automated testing tools are often used to streamline these processes, helping manufacturers detect and fix issues quickly.
The role of certification and compliance
Certification is a key part of the process. Achieving certifications like FIPS or ISO 27001 shows that a semiconductor device meets high-security standards and can be trusted for use in regulated industries. For example, FIPS 140-2/3 certification is a must for devices used by federal agencies in the U.S., while ISO 27001 certification is becoming a global benchmark for companies wanting to show their commitment to information security. These certifications aren’t just about meeting regulatory requirements; they help build trust with customers, ensuring that the devices they use are secure and capable of standing up to emerging threats.
Challenges in merging security standards with firmware validation
Integrating standards like FIPS and ISO 27001 into the firmware validation process comes with its share of challenges. For starters, these standards are constantly evolving. As new threats and technologies emerge, the standards must adapt, requiring semiconductor manufacturers to keep up with regular updates and revisions. Staying on top of these changes can be resource-intensive, but it’s crucial to ensure that devices stay secure.
Another challenge is the need to balance security with performance. As semiconductor devices grow in power and versatility, firmware validation needs to make sure that robust security measures don’t end up slowing down performance. Manufacturers also face the complexity of meeting regional security standards. Different markets may have varying regulatory requirements, so manufacturers must adapt their devices to comply with different standards around the world while maintaining performance and security.
Innovations in firmware validation
Despite the challenges, innovations are making firmware validation more efficient. Automated testing tools, integrated into continuous integration (CI) pipelines, speed up the detection of vulnerabilities and compliance gaps. These tools take care of repetitive tasks, allowing engineers to focus on more complex validation issues. On top of that, advancements in cryptographic techniques, like quantum-safe encryption, are helping secure devices against emerging threats like quantum computing.
Click here to read the full article in Semiconductor Digest magazine.